Introduction to Quantum Computing
RSA
The RSA algorithm involves four steps:
- Key Generation (a public key
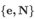 and a private key
and a private key 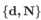 )
) - Key Distribution,
- Message Encryption
- Message Decryption

Terms:
- m = plaintext message
- c = unreadable ciphertext
- e = Public Key
- d = private key
- N = large number which is the product of two prime numbers
- p = prime number
- q = prime number
- r = periodicity
Formulas:
- Modular Exponentiation
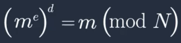
- Encrypted ciphertext

- Decrypt ciphertext
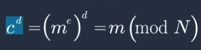
- Order finding
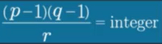
- choose e

- solve for d
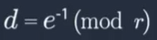 or de mod r = 1
or de mod r = 1
Example:
- Key Generation
- choose prime numbers for "p" and "q" at random --- p = 2, q = 5
- calculate "N" = p * q --- N = 2 * 5 = 10
- determine "e" and "d" -- need to determine the periodicity property
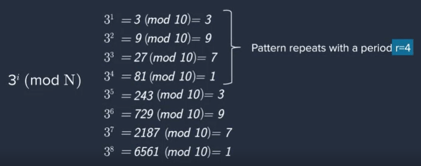
(p-1)(q-1) / r = integer
(2-1)(5-1) / 4 = 1*4 = 4
this checks compared to the observed period "r"- now, determine "e" and "d"
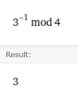
first choose an "e" such that 3 <= e <= r
References:
- Cryptography:
https://en.wikipedia.org/wiki/Cryptography - RSA (cryptosystem):
https://en.wikipedia.org/wiki/RSA_(cryptosystem) - RSA Algorithm in Cryptography:
https://www.geeksforgeeks.org/rsa-algorithm-cryptography/ - What is RSA encryption and how does it work?:
https://www.comparitech.com/blog/information-security/rsa-encryption/ - Verizon plans to fight quantum attacks with these 'quantum-safe' VPNs:
https://www.youtube.com/watch?v=6_b2y-ytHvM - Quantum Cryptography:
https://en.wikipedia.org/wiki/Quantum_cryptography - Quantum Cryptography/Encryption in 2022: In-Depth Guide:
https://research.aimultiple.com/quantum-cryptography/ - Qiskit:
https://qis